How the initiative to make the internet secure gone wrong?
SSL was supposed to protect you..
How the initiative to make the internet secure gone wrong?
In: Security, Cybersec, Infosec, IT SecurityTaking into account the main purpose of SSL is to ensure an encrypted channel of communication between server and client, ensuring both authenticity and integrity via trust chain as well prevention of decrypting without a proper Public / Private key pair.
In its essence, modern cryptography provided a viable solution to:
- Ensure authenticity of server
- Prevent man in the middle decrypting of sensitive informations
- Ensure you can’t reach the origin server in direct.
- Ensure encryption takes place at the edge of Cloudflare. In other words, re-encryption, or if you like, a “Man in the middle”.
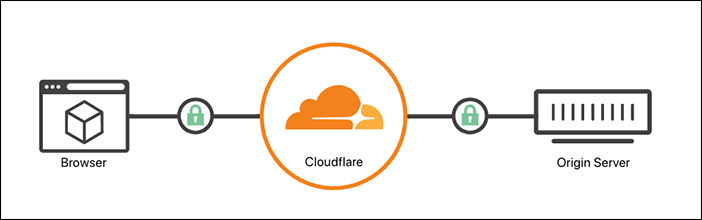 The main “problem” back in the days, was the fact that encryption takes place prior to Layer 7 headers are sent, including the virtual host name requested. This made it impossible to host multiple websites using the same pair of keys or at least without listing all hostname within these 2048 bits of certificates.
And a problem has been “Solved”. Implementing Server Name Indication (SNI) as an extension to TLS allowing clients to indicate which hostname is trying to connect to within the early stage of handshaking process.
SNI has been born!
The main “problem” back in the days, was the fact that encryption takes place prior to Layer 7 headers are sent, including the virtual host name requested. This made it impossible to host multiple websites using the same pair of keys or at least without listing all hostname within these 2048 bits of certificates.
And a problem has been “Solved”. Implementing Server Name Indication (SNI) as an extension to TLS allowing clients to indicate which hostname is trying to connect to within the early stage of handshaking process.
SNI has been born!
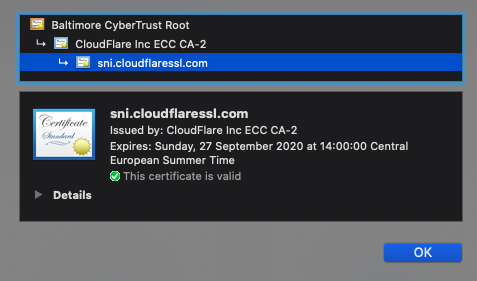 Finally, a single IP could support millions of websites “protected” by Cloudflare.
With all the respect of Google’s attempts to make web more secure, what we ended up is:
Finally, a single IP could support millions of websites “protected” by Cloudflare.
With all the respect of Google’s attempts to make web more secure, what we ended up is:
- Inability to validate the origin server is what is supposed to be. It’s up to Cloudflare edge.
- Inability to prevent man in the middle considering re-encryption takes place by design.
Nope, obviously the push went without any response although millions of sites were affected. In other words, let’s try to cover up. What’s your opinion. Did we made a progress considering the starting point of:Hey @letsencrypt boys and girlz what happened tonight with an outage? Is there anything worth knowing in regards to a bug fixed and deployed?#letsencrypt #Linux #infosec #ITSecurity #CyberSecurity #CyberSec
— Stefan Ćertić (@cs_networks) February 29, 2020
- Ensuring authenticity
- Preventing man in the middle
- Hiding and preventing authenticity
- Has wide open hands for men in the middle decryption.

Join the talk
Share your toughts on the subject or whatever you would like to know.