VPN Protection that really protects
Want a secure transmission? Here is a simple one.
VPN Protection that really protects.
In: Credit Card, Fraud, POS, Payments, PINWant a secure transmission? Here is a simple one that solves most of your troubles.
With increasing CPU power, Statistical Analysis becomes far more than something you would find in geeky math books. A distributing computing clusters equipped with multiple physical CPU nodes and terabytes of RAM would be able to crack your encryption keys in days or even minutes.

A simplest possible proof of concept would be a MIT double pendulum project, a software that managed to learn the gravitation constant only by analyzing motion vectors of two interconnected pendulums. Read the paper here.
What’s in common that governs the whole motion vectors of these two interconnected bodies. – A gravitation constant. Software basically uses a tension, a mass and vectors to determinate the constant. And it’s found – within minutes. We needed millions of years to measure it – while software needed few minutes to derive without prior knowledge.
Enough math, let’s get back to Computer Science for all of you hack-minded friends, and what it has to do with all your passwords and VPN keys that could be derived out of raw tcp dumps.
Basically, the very same principle, although more complex is taken in one way encryption, which is possible to the same extent as the truly random number generator utilizing digital design. Is there such a thing?
By getting close to a point of being able to analyze any series of known inputs and outputs in order to generate possible set of operations performed deriving the correct results, it’s only a matter of minutes, days, or years to analyze and derive keys. With recent developments in BIG Data, things are not so far away.
Let’s try an interesting setup to propose a solution to this type of VPN attacks.
What we will be using is standard IPSec Tunnels, 20 years old technology - 802.3ad (Link Aggregation), making multiple diverse physical links. The purpose of digitalization was to perfectly reproduce signals without losses and distortion. Instead of going the way of physical random generator, let's exploit the fact timings are not perfect, physical distances between routers, round-trip times and losses.

The retransmission of missing ACK's will take care to make statistical analysis impossible, and re-key of each dropped port without service degradation (as other bonding members will take over) will make it further impossible, as the key is changed frequently.
What we adding here is something that’s truly random. Network congestion, interruptions that happens due to a nature and imperfect design of circuits as well as different timing of diverse links and all the equipment queues and loads all along.
The idea to add true randomness by inducing as many environmental factors as possible. While environmental factors are not random by nature, aggregating enough of them so it get's towards the infinity, makes statistical analysis impossible.
And that's where Dichotomy paradox kicks in. To travel the path from A to B, at one point you need to be in the middle. And in the middle of the middle. While nothing is random, you are in need of infinite known variables - making it... a random.
Getting down to earth: even under assumption you are able to obtain full TCP dumps from 'n' different ISP's, (and to know there are 'n', statistical analysis would need to take a place prior to knowledge of what you will be performing statistical analysis on).
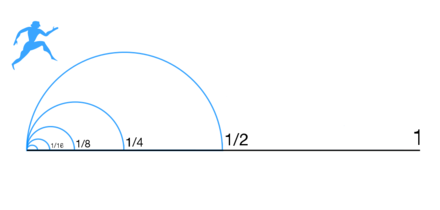
A simple combination of IPSEC, Multiple Wan's and 802.3ad Link Aggregation could make you safe from transmission examination.

Join the talk
Share your toughts on the subject or whatever you would like to know.